Legacy Python Bootstrap Scripts Pose Domain-Takeover Risk in PyPI Packages
Cybersecurity researchers have identified a significant security risk involving legacy Python bootstrap scripts used in multiple packages on the Python Package Index (PyPI). These vulnerable scripts could allow attackers to carry out a domain takeover attack, potentially compromising the software supply chain. The discovery highlights the ongoing risks present in older Python packages that rely on outdated bootstrap files.
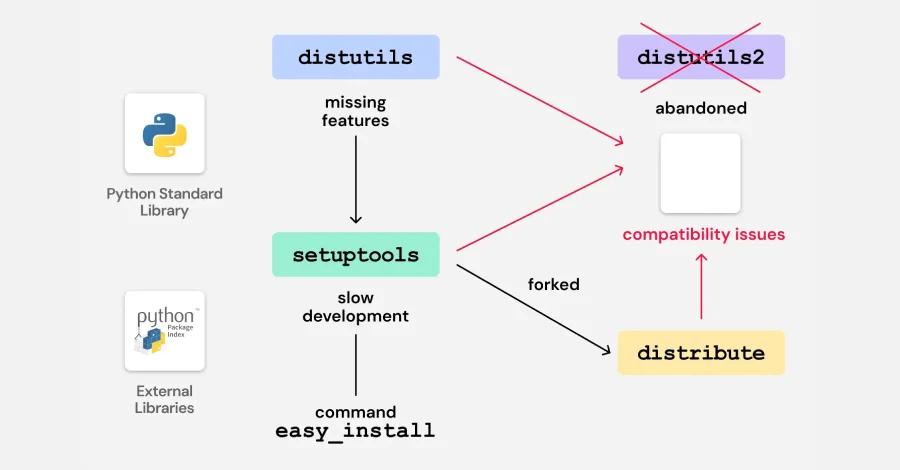
The issue was uncovered by ReversingLabs, a company specializing in software supply chain security. They found the vulnerability within bootstrap files associated with a build and deployment automation tool called “zc.buildout.” This tool is widely used to automate the build process for Python projects, but its legacy bootstrap scripts contain weaknesses that could be exploited by malicious actors.
Understanding the Domain-Takeover Risk in Legacy Python Bootstrap Scripts
The vulnerability stems from how the legacy Python bootstrap scripts handle external dependencies and domain references. Attackers could potentially take control of domains referenced by these scripts if those domains have expired or are otherwise unclaimed. By registering such domains, an attacker could inject malicious code into the build process of Python packages that depend on these legacy scripts.
This type of domain takeover attack poses a serious threat to the integrity of the Python software supply chain. Since PyPI is a central repository for Python packages, any compromise could have widespread effects, impacting numerous projects and developers relying on these packages. The risk is particularly acute for packages that have not been updated to remove or replace the vulnerable bootstrap scripts.
Mitigating the Supply Chain Risk from Legacy Python Bootstrap Scripts
Addressing the domain-takeover risk requires package maintainers to review and update their build and deployment processes. Removing or replacing legacy bootstrap scripts like those from zc.buildout can help close the vulnerability. Developers should also monitor the domains referenced in their build scripts to ensure they remain under trusted control and are not susceptible to takeover.
The discovery by ReversingLabs serves as a reminder of the importance of maintaining secure and up-to-date build environments. Legacy Python bootstrap scripts, while once useful, now represent a potential attack vector that can undermine the security of the Python ecosystem. Proactive measures are essential to protect against supply chain compromises stemming from these outdated components.
In summary, legacy Python bootstrap scripts present a domain-takeover risk that could lead to supply chain compromises on PyPI. The vulnerability found in zc.buildout’s bootstrap files underscores the need for vigilance and modernization in Python package maintenance. By addressing these risks, the Python community can help safeguard the integrity of its software supply chain.
For more stories on this topic, visit our category page.
Source: original article.